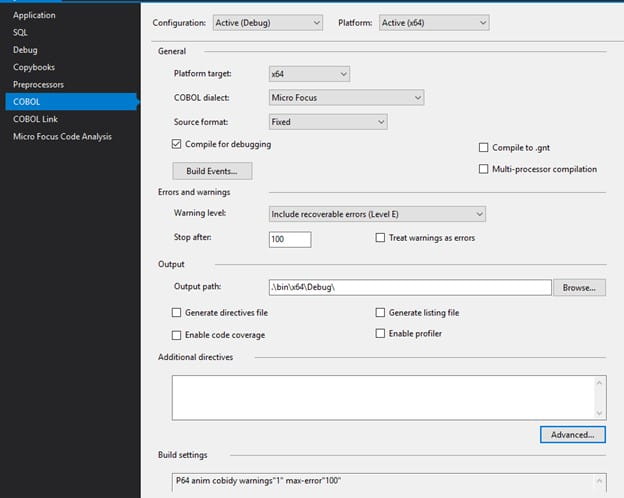
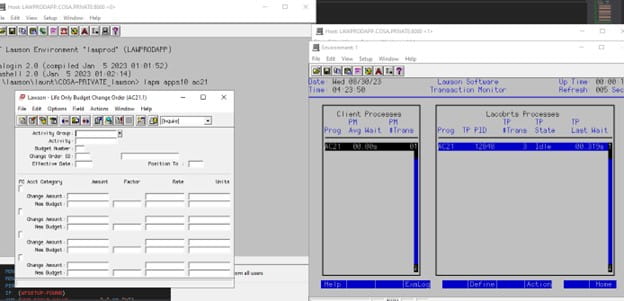
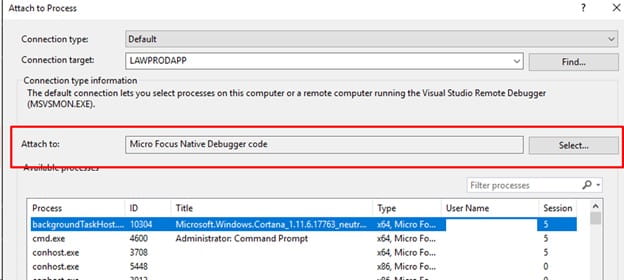
Sometimes compiling for trace, or adding display statements to a 4GL program, just doesn’t quite get you far enough with debugging. Lawson is installed on a MicroFocus COBOL for Visual Studio, which can be debugged using Visual Studio. Here are the steps to set up the debugger for a Lawson form:
- First, compile your program for debug (i.e. lawcmp -D <pdl> <system> <program>)
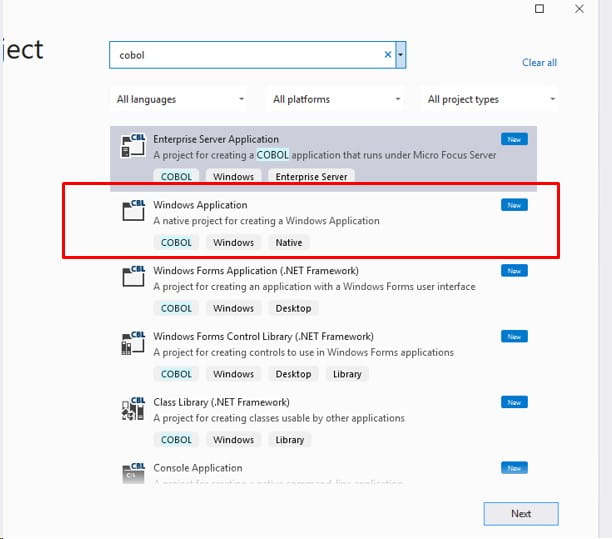
- Create a new Windows Application project for COBOL.
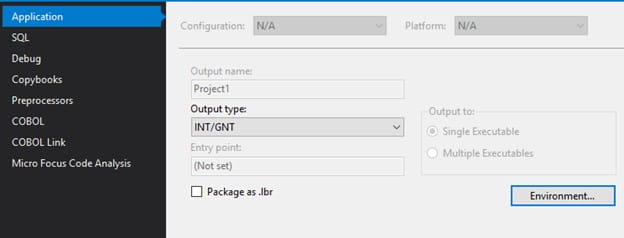
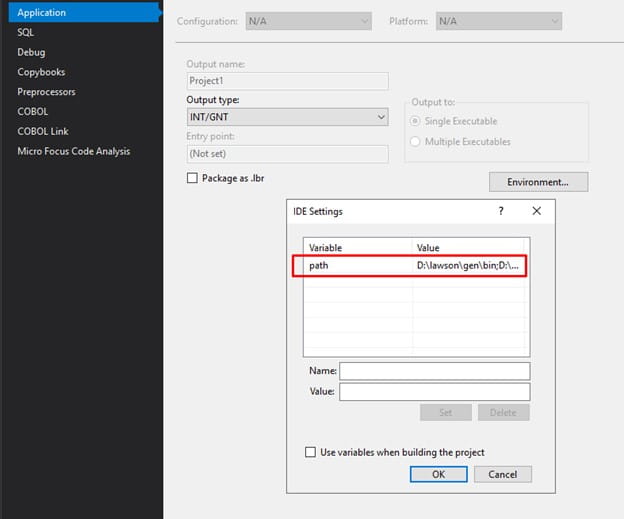
- Configure the application for Output Type INT/GNT, and open the “Environment…” to set a Path variable. This variable should contain <GENDIR>\bin;<JAVA_HOME>\jre\bin\server;<LAWDIR>\<pdl>\obj;<LUU_DIR>
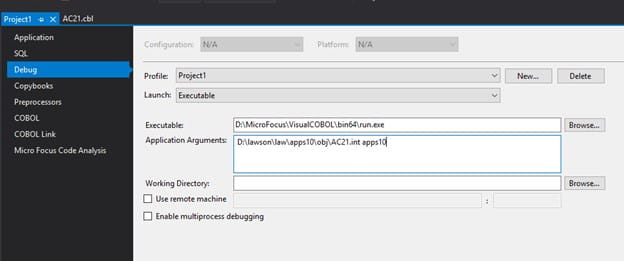
- Under Debug, set the project to launch an executable. The executable should be <MF_HOME>/bin64/run.exe, and the Application Arguments should be <LAWDIR>/<pdl>/obj/<debug program>.int <pdl>
- On the COBOL tab, set the configuration to Active (Debug) and the platform and platform target to your current server platform. Set the COBOL dialect to Micro Focus. Set the output path to .\bin\x64\Debug
- Add the “.cbl” file to the Visual Studio project that was generated from your compile in debug mode (step 1).
- You can set break points in that cbl file
- Now, it’s time to debug your form. Open the application using LID (lapm <pdl> <program code>)
- In a separate LID session, run the command tmmon and make note of the pid for your Lacobrts process.
- Now, in Visual Studio, select Debug > Attach to Process
- Select the process you identified in tmmon (it should be a run.exe). Now you can perform the process that you were trying to debug, and Visual Studio will stop at the break point you set.
When trying to install a CTP you encountered the below error:
“Error – failed to uncompress “patch.tar.Z” file.” or “patch.tar already exists; not overwritten”
There’s a possibility of encountering this error due to the presence of an extra patch.tar file stemming from a prior or simultaneous CTP installation.
Upon executing the tar command, ensure that within the <versionfiledir> directory, where you’ve unpacked the CTP, only three files pertain to this CTP. Verify that you have obtained the following trio of files:
– x.x.x_patch_CTPnumber.readme.html
– Versions
– patch.tar.Z
Clear out any past CTP files from this location, particularly any patch.tar files, and proceed to rerun the lawappinstall.
For UNIX systems:
It’s possible that the lawson user lacks write permissions to a directory higher up in the hierarchy. The entire directory where the decompression is taking place should have permissions set to 777.
For Windows:
If you encounter this error on a Windows server, it may be due to spaces in the folder names along the path to the versions directory. If this is the case, you’ll receive a “failed to uncompress” message.
To resolve this, replace spaces with underscores (_) or use folders without spaces in their names, then proceed to rerun the lawappinstall command.
Typically when installing CTPs it is recommended to have a new directory for each CTP install.
Problem:
Error receiving a Purchase Order on MSCM handheld. The error message reads: “PO not Available. PO contains no open PO lines.”
However, the PO has open lines in PO20.1.
Resolution:
This error occurs when a PO’s Ship To location is not designated as a “Receiving, Ship To” location in MSCM.
To resolve this error, follow the steps outlined below:
From the MSCM web application, do the following:
- select Location Management.
- Select Modify from the Locations drop-down menu.
- Enter the Ship To location in the Location Id field.
- Click on the Search button.
- Check the Receiving, Ship To box.
- Click on the Modify button.
- Click on the Done button.
Problem: Users are not able to log into MSCM on handheld devices. They are able to access the MSCM console through browser, but not directly on the handhelds.
Before we get to the solution, consider the handheld timeout settings. The Timeout setting is the amount of time the handheld will attempt to connect when sending/receiving information. It can be set by selecting the number of seconds in the counter. Note that the maximum timeout setting is 3600 seconds while the minimum is 60 seconds.
The resolution for users who are not able to log into MSCM on their handheld devices is to truncate the LAWSON_USER table and stop & restart MSCM server to force re-syncing users. You shouldn’t have any more problems logging in on handheld devices.
Issue: I possess Design Studio forms from the previous version of Lawson System Foundation (LSF) and Infor Lawson for Ming.le. How can I ensure their compatibility with my current LSF and Infor Lawson for Ming.le environment?
Solution: A Migrate Tool has been provided, starting from specific LSF versions and patches onwards:
– LSF 10.0.4, JT-651295, PORTAL.DIR/utility/upgradeCustomContent.htm version 10.0.4.0.747 minimum
– LSF 10.0.5, JT-651295, PORTAL.DIR/utility/upgradeCustomContent.htm version 10.0.5.0.746 minimum
– LSF 10.0.6, JT-651295, PORTAL.DIR/utility/upgradeCustomContent.htm version 10.0.6.0.745 minimum
– Included in the base release for LSF 10.0.7 and newer versions
Steps to follow in LSF 10.0.4, 10.0.5, and 10.0.6 with the specified patches, as well as in the delivered release of LSF 10.0.7 and above:
To review the existing Design Studio forms:
- Log in to Infor Lawson for Ming.le with a Portal Administrator account.
- Navigate to Custom Content Tools.
- Select Migrate Custom Content.
- Choose Analyze | Custom Forms.
To update the existing Design Studio forms:
- Log in to Infor Lawson for Ming.le with a Portal Administrator account.
- Navigate to Custom Content Tools.
- Select Migrate Custom Content.
- Choose Migrate | Custom Forms.
Please note:
This process won’t alter the “XMLGenBy=”xscrgen 10.0.7.0.1240 2016-03-09 08:32:37″” listed in the XML of the Design Studio form. Instead, it will append this tag to the first line: dateupgrade=”1443633109897″. To ascertain the date of the upgrade, visit https://currentmillis.com/ and input the associated value.
To review the current Design Studio forms with custom JavaScript:
- Log in to Infor Lawson for Ming.le with a Portal Administrator account.
- Navigate to Custom Content Tools.
- Select Migrate Custom Content.
- Choose Analyze | Custom Script.
Please note:
There isn’t a migration process for Custom Script. This requires manual handling based on the information from the Analyze step.
Below is a cheat sheet for batch status numbers & their descriptions:
There are several use cases for querying the QUEUEDJOB table in GEN in order to get batch job details, such as status and run times. The status is stored as a numeric value, not the actual status that is seen in the GUI. It can also be useful to be able to map it to the description. Here are the batch job status numbers with their descriptions:
# 0 – Running
# 30 – Waiting
# 31 – Waiting Step
# 32 – Waiting On Time
# 33 – Waiting Recovery
# 34 – Needs Recovery
# 35 – Invalid Parameters
# 36 – Queue Inactive
# 37 – On Hold
# 60 – Recurring Skipped
# 61 – Recovery Deleted
# 62 – Cancelled
# 63 – Normal Completion
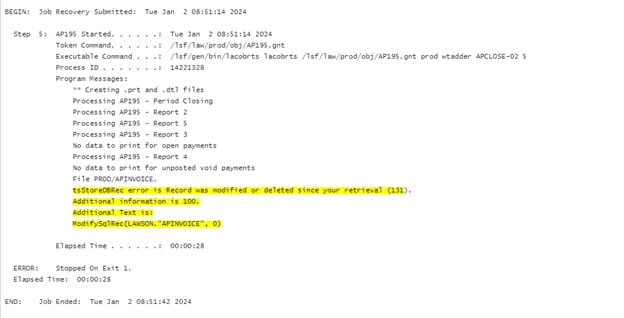
Jobs is in needs recovery with error
tsStoreDBRec error is Record was modified or deleted since your retrieval (131). Additional information is 100. Additional Text is: ModifySqlRec
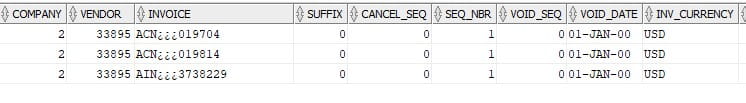
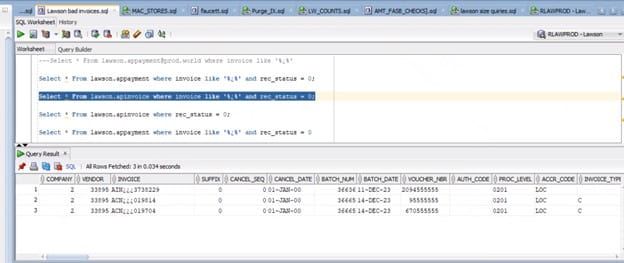
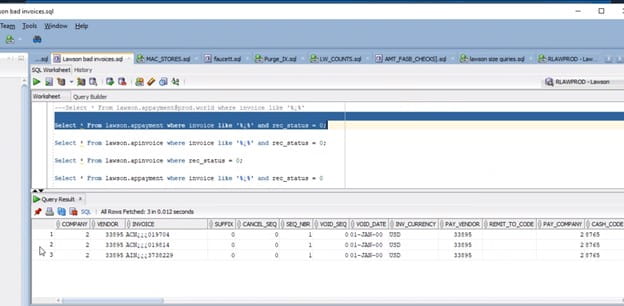
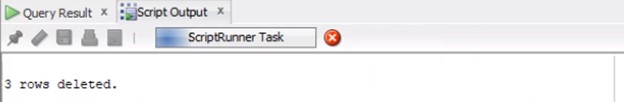
There are 3 bad invoices in APINVOICE and APPAYMENT with no distribution records in APDISTRIB.
The 3 bad records are as follows
Resolution:
In SQL Manger, query the APINVOICE and APPAYMENT files for any invoices with bad name format as below:
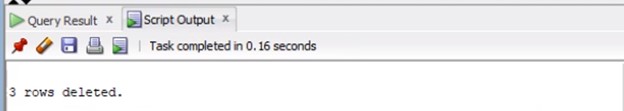
Verify these records do not have any distributions records in APDISTRIB. If not, Delete these bad invoices.
APPAYMENT
APINVOICE
Run commit to commit the changes
Go into lawson and recover the job
Keywords:
PROBLEM:
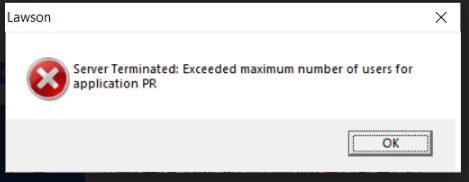
I continue to receive the following error message when attempting to log into LID:
That indicates a license issue.
so I ran licsta -r and found the license file is corrupt because it reverted to client 9999.
> licsta -r
Active License Status For Client 9999
License Code/ Active Licensed Highest
Application Users Users Use Expiration Date
———– —— ——– ——- —————
default 2 7 Thu Aug 31 13:25:17 2023
PR 2 Not Licensed
LP 1 Not Licensed
HR 1 Not Licensed
un 4 10 13 Sun Sep 17 10:39:42 2023
Run licsta -f and verified the file is corrupt.
> licsta -f
File [E:\lawson\law\system\license] not copied to E:\lawson\law\system\tmplicense] – Error [33]
Unable to Read License File Header – File May Be Corrupted
You will need to request a new software license key and re-install the license file.