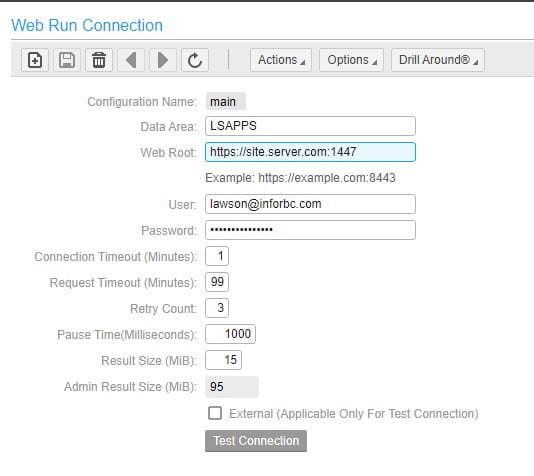
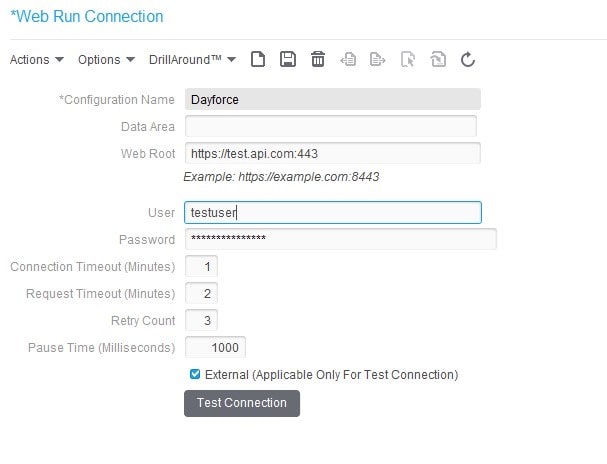
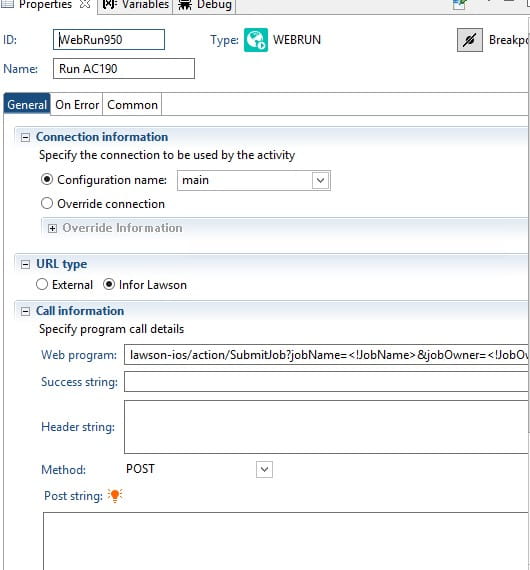
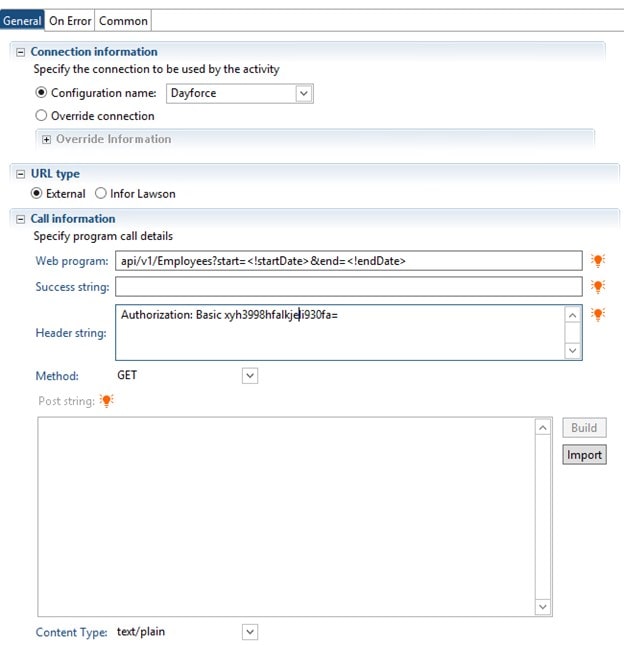
Federal law generally requires organizations in regulated industries to have written data retention policies. For example, if an organization operates in a regulated industry where data must be retained for seven years, the company’s retention policy must specify and enforce the specified seven-year retention period. With established policies, organizations can comply with regulatory requirements that require the storage of various types of data. There are many operational advantages to implementing a data retention policy, and many companies have policies in place to ensure they do not violate local, state, and federal laws, as well as various industry regulations.
Both internal and external policies dictate the rules and regulations for data retention, and it is critical that organizations can manage a comprehensive data retention program that meets both requirements. As healthcare organizations create and manage large amounts of electronic data from a variety of sources, record keeping is becoming an increasingly important and complex aspect of information management. Compliance with HIPAA records retention requirements is critical for both medical file storage software developers and healthcare professionals. Given the wide range of varying federal and state health record retention and destruction requirements, it is imperative to follow best practices to ensure compliance with HIPAA and state standards.
HIPAA requires each provider and company that manages protected information to develop a policy for the retention and deletion of medical records. While the HIPAA Privacy Policy does not contain requirements for the retention of medical records, the HIPAA Privacy Policy does include requirements for how data is stored. Statewide, there is no HIPAA medical record retention requirement, and in many cases the state legislature determines the retention period, in which case HIPAA does not take precedence over state law.
State laws may also require medical records to be retained for a longer period than HIPAA retention standards and background data. Any state law that requires a stricter retention period for medical records than HIPAA requirements remains in effect and supersedes federal law. There is actually no HIPAA medical records retention period, which means there is no period of time that a healthcare provider must keep a patient’s medical records before those records can be deleted or destroyed.
Following the HIPAA medical records and record retention period, HIPAA requires the secure destruction of physical and electronic forms of PHI to prevent unauthorized disclosure of PHI. HIPAA record retention rules apply when an entity covered by HIPAA collects information related to medical services or payment for medical services.
Health insurance providers must comply not only with the HIPAA retention rules, but also with the Financial Industry Regulatory Authority (FINRA) rules. In addition to the HIPAA requirements, the healthcare industry is subject to data retention requirements set by the Centers for Medicare and Medicaid Services (CMS) and state laws.
Healthcare organizations are subject to the data retention requirements of the Health Insurance Portability and Accountability Act, and organizations that accept credit cards must adhere to the data retention and deletion policies of the Payment Card Industry Data Security Standard.
For example, for companies in the healthcare sector, one unique regulatory requirement is the Health Insurance Portability and Accountability Act (HIPAA), which governs medical data. There are requirements for how long HIPAA records must be kept while states regulate medical record storage requirements. Although the Health Insurance Portability and Accountability Act (HIPAA) does not contain universal health record retention requirements—instead, they vary from state to state—it does include specific HIPAA-related record retention language. Approved in 1996 to protect health insurance coverage for people who were off work, HIPAA is now known as the document that also guarantees health record retention policies, defines the parties and documents involved, and is the primary document that providers use when creating. internal physician retention policy.
Although HIPAA stipulates that medical records must be kept “for as long as necessary” and does not set time limits, what this means is that healthcare professionals must instead look at the statute of limitations applicable to their condition, as well as the rules required by any regulatory authorities. While record retention requirements are part of the broader HIPAA compliance policy, they should be considered first by your software solution or service provider. In addition to maintaining HIPAA records, insurance companies may be subject to the complexities of FINRA, while employers may need to comply with the record keeping requirements of the Employee Retirement Income Security Act and the Fair Labor Standards Act.
As stated earlier, HIPAA protections apply to many different types of PHI, including patient records, diagnostic images, prescription records, billing records, etc. and require retention of all protected health information for a period of six years from the date of publication, creation or the date of its last effective date, whichever is later. In the UK, the Health and Social Care Records Practice Code of Practice 2016 specifies that anyone working with or in the National Health Service (NHS) is required to keep medical records for 20 years after the last contact with a patient – 8 years after death or up to 25 years after the birth of the last child on maternity documents. Customer records, contracts, financial information, health data, third party data, employee records, spreadsheets, emails, and more are typically subject to data retention policies, regardless of sector.
Organizations should conduct a thorough audit of the data they hold, from patient and employee records to policies and procedure documentation. In many modern health care organizations, the ongoing maintenance of medical records is a discipline that requires specialized personnel and skills. Depending on the industry and business, several laws and regulations may affect data retention policies and may require overlapping or even conflicting requirements regarding how long certain types of data should be retained or what you need to do with it when it’s time to delete it.
If you’re migrating to a new system and need to properly archive your data, you should consider your options. One option is to keep your old system around for inquiry purposes only, though this can prove to be costly and complicated. Another option is to dump all your data into a data lake and worry about it all later, but this fails the most basic test for a data archive solution; accessibility. Luckily, there is a third solution.
The APIX serverless framework, based on the AWS serverless stack has opened up incredible possibilities for inquiry only applications never before possible without a substantial investment in infrastructure. Clients can now provision a web based, lightweight, data archive solution and migrate all their data within days rather than months and at a fraction of the cost of the other solutions with none of the risk. Find out how the APIX serverless framework can help you meet all your Lawson data archive needs and eliminate the legacy servers for good.