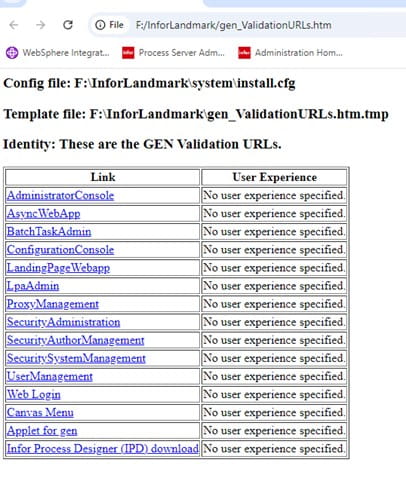
Cloud computing offers businesses increased accessibility and flexibility, but migrating digital assets from existing servers can pose security risks if not executed carefully. To prevent data breaches and compliance issues, it’s essential to follow best practices in cloud security, guided by experienced professionals. A recent article on Analytics Insight discusses four main challenges organizations face when securing data during a cloud transition. First, data privacy becomes complex as sensitive information moves outside traditional on-premises environments, raising compliance concerns. Second, ensuring proper access control is critical; organizations must manage identities and permissions effectively to prevent unauthorized access. Third, data leakage risks increase during migration, requiring robust encryption and monitoring measures. Fourth, maintaining consistent security policies across hybrid or multi-cloud setups is challenging, leading to potential vulnerabilities. The article emphasizes the importance of a comprehensive security strategy that includes data encryption, identity management, and continuous monitoring. It also highlights the need for organizations to understand their data flow and adopt best practices for data governance. Implementing strong authentication methods and leveraging automation can help mitigate risks. Regular security assessments and staff training are essential to adapt to evolving threats. Cloud service providers offer security tools, but organizations must actively configure and manage these resources. Additionally, transparency and compliance with regulations like GDPR are vital during the transition. The article concludes that proactive planning and a layered security approach are key to safeguarding data in cloud migrations. Overall, addressing these challenges ensures data integrity, confidentiality, and compliance in the cloud.