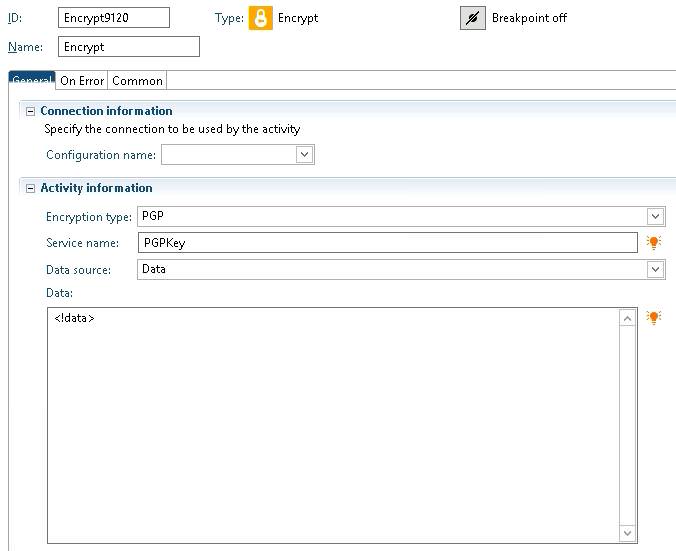
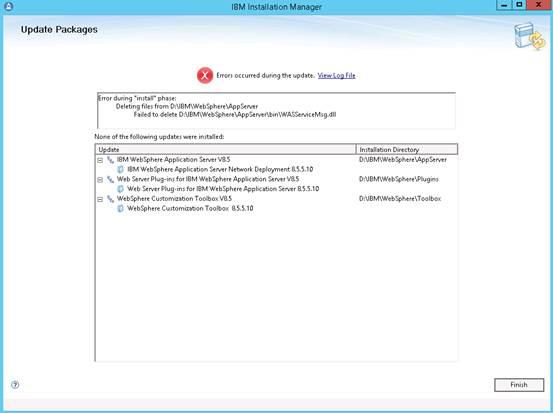
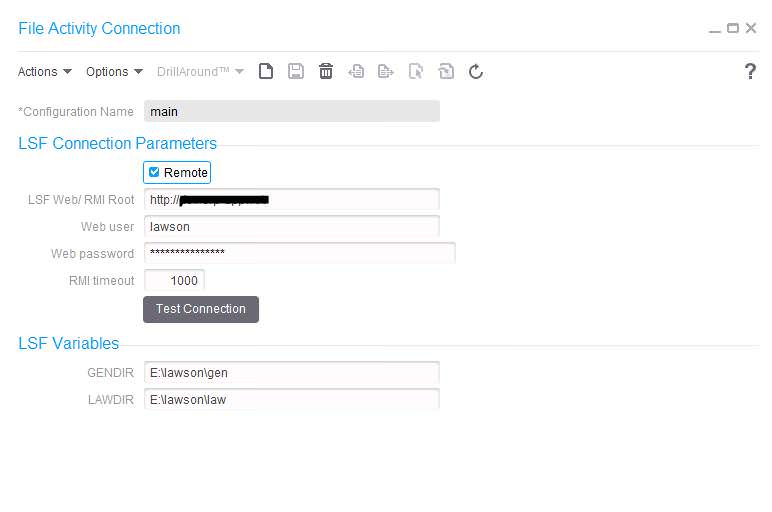
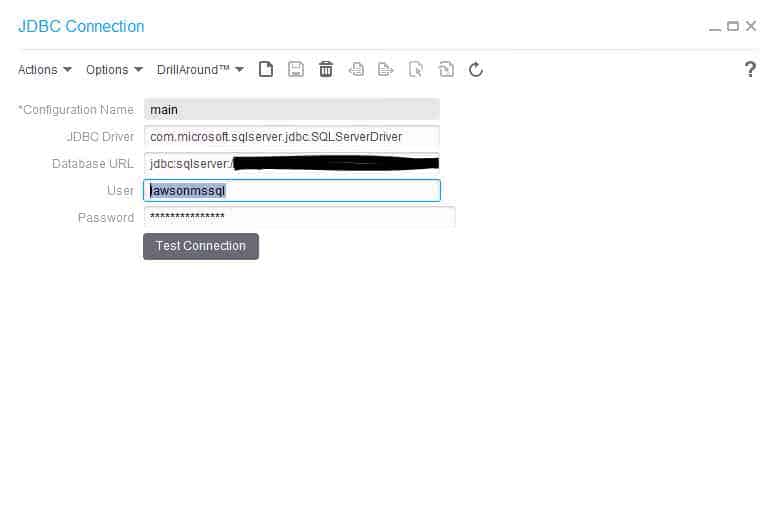
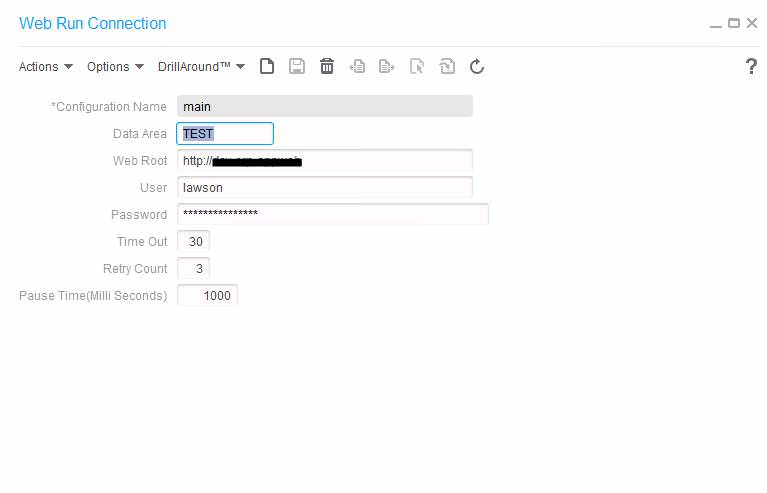
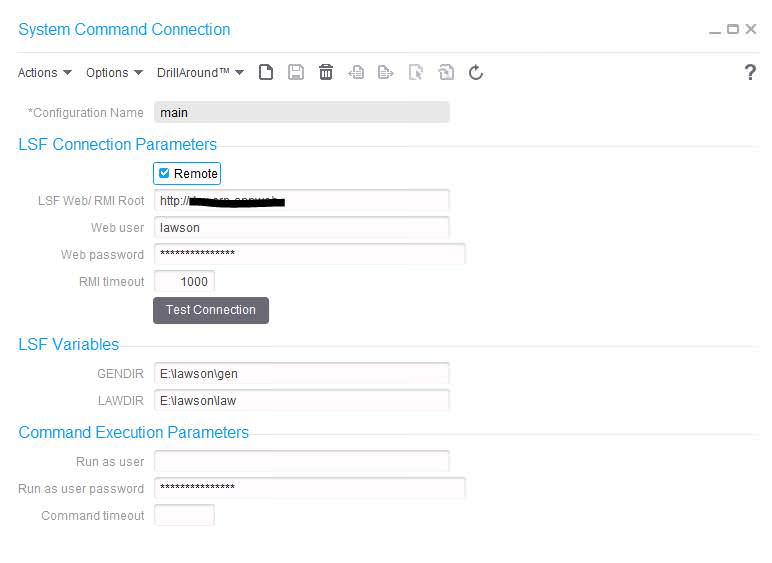
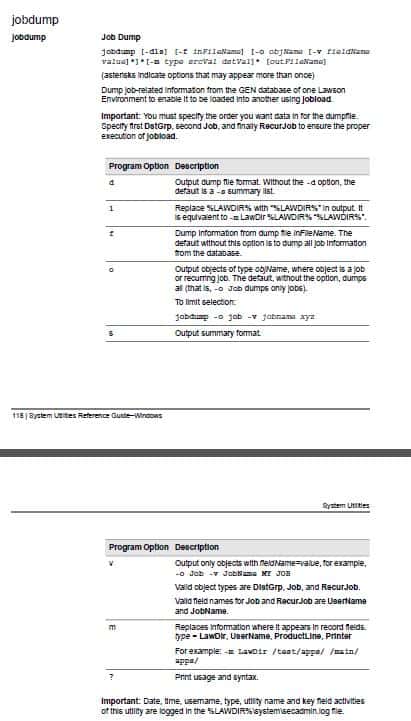
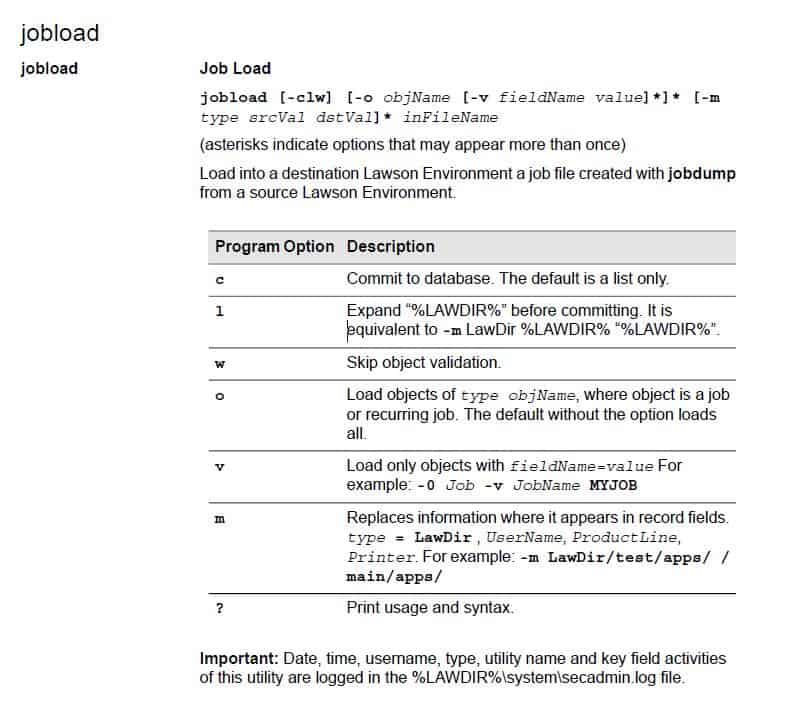
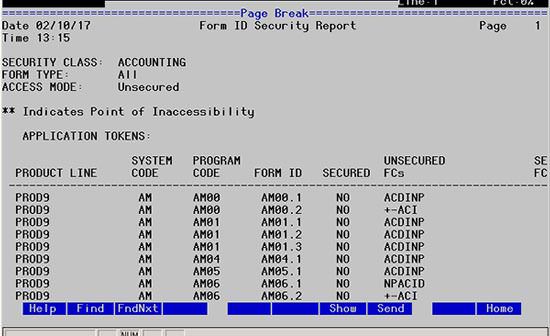
These nodes can be used to encrypt/decrypt data or files for secure transmission. Before you begin, you must have a PGP key pair generated by a network security administrator.
Both nodes have the same properties:
- Configuration name – Select the configuration you wish to use for this encryption. If the configuration name is blank, the default will be used.
- Encryption (or Decryption) Type – PGP is the only encryption type available
- Service Name – This is the name of the service that was assigned for the generated key pair.
- Data Source – Encrypt raw data, or provide a file name to encrypt the contents of the file.
- Data – Provide the data or the full path of the file that will be encrypted.