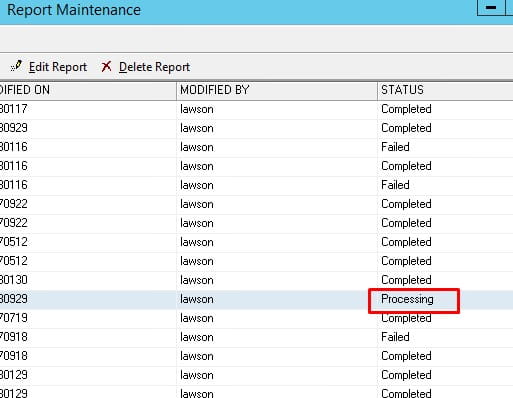
Steve Banker, Vice President of Supply Chain Services at ARC Advisory Group, shares a post on Forbes summarizing Infor’s strategy for differentiating their solutions at the Innovation Summit held on March 18-19th. According to Banker, several top executives laid out Infor’s strategy for differentiating their solutions based on their approach to technology, product development, and customer service. Infor, with anticipated revenues of $3.4 billion for 2024, is the third largest supplier of enterprise resource planning software applications. Below is a summary of topics covered and the tech giant’s approach to each one.
Infor’s Approach to Industry Specific Solutions. “The ERP market is making the transition to the Cloud. ERP firms like Infor, Oracle, and SAP – or supply chain software companies – like Manhattan Associates and Blue Yonder – have produced multitenant cloud solutions. Some of these companies are further along in their journey to convince their customers to move to a multi-tenant solution than others. Multi-tenancy, also known as ‘public cloud,’ is a software architecture where multiple instances of an application run on the same physical server. A public cloud solution has two key advantages. It can be much quicker to implement, so customers have a quicker payback period. Customers can also continue to get new functionality without going through a painful upgrade process. With traditional software, the upgrade process was so painful that many companies rarely, if ever, upgraded. But for customers to fully achieve these benefits, they need to commit to forgoing customization. Increasingly, large enterprises have decided to do just that. But where Infor is different from the largest ERP suppliers in the market is that instead of building one public cloud solution that serves all their customers, they have built three separate public cloud solutions. Each public cloud solution is designed to support a limited number of industries.”
Infor Success Teams. “Infor has developed customer success teams. A customer has a dedicated team that is headed up by a person with deep knowledge of the customer’s industry. The team is evaluated, in part, based on their ability to generate value for that customer over time. These teams’ job is to ask, “did the customer achieve the return on investment they were aiming for with their implementation?” Before an implementation begins, the potential is mapped. Industry best practice processes will be examined. If the customer commits to this out of the box process, what is the value they will gain? The value derived from the implementation will depend upon the customer achieving certain key performance indicators or key value indicators across all the ‘best practice’ processes. The software architecture allows the value to be measured and those metrics are visible to both the customer and the success team.”
Laying the Groundwork for Customer Success. “The customer success program, while more complete, does not sound radically different then what other software vendors have described as how they work with key customers. What is different is that the groundwork for achieving success is laid out during the sales process. “The implementation really starts in the sales cycle,” Frank Resink, the executive vice president of professional services, said. For food & beverage, Infor has up to 900 processes. They go through these processes with potential customers and define the value drivers. Infor works with the customer to validate which out of the box process will drive value and identify which out of the box processes would need to be adapted.”
Is the New Approach Working? “So, is this new approach, which is continuing to be scaled up to include more and more customers, really working? It is working for Infor. Solutions based on the public cloud – software as a service customers – have grown at a compound annual growth rate of 28.3% over the past three years. According to the company, for many customers, the speed of the implementation is now often limited by a customer’s ability to handle culture change rather than by integration, data cleansing, or configuration hurdles. There is also evidence it is working for customers. In 2020, Infor SaaS customers had an attrition rate of 8.4%. By 2023, attrition among these customers had fallen to 3.2%. Infor’s strategy for differentiating their business from competitors like SAP and Oracle is to be more industry focused. That industry focus, in turn, supports a truly differentiated approach to ensuring that their customers get ongoing value from the business applications they have purchased.”
For Full Article, Click Here