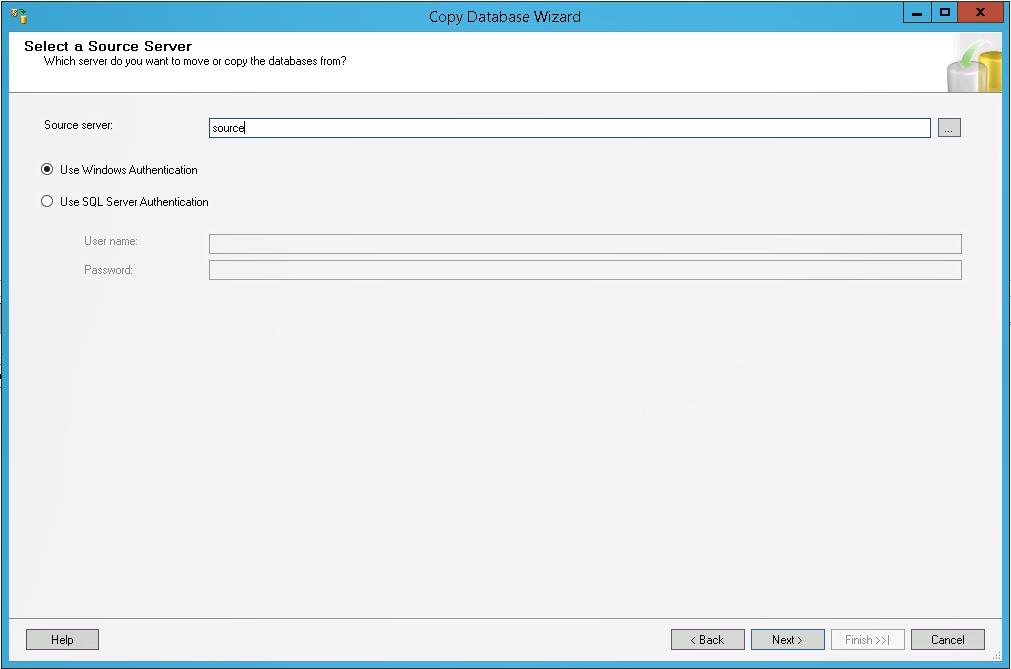
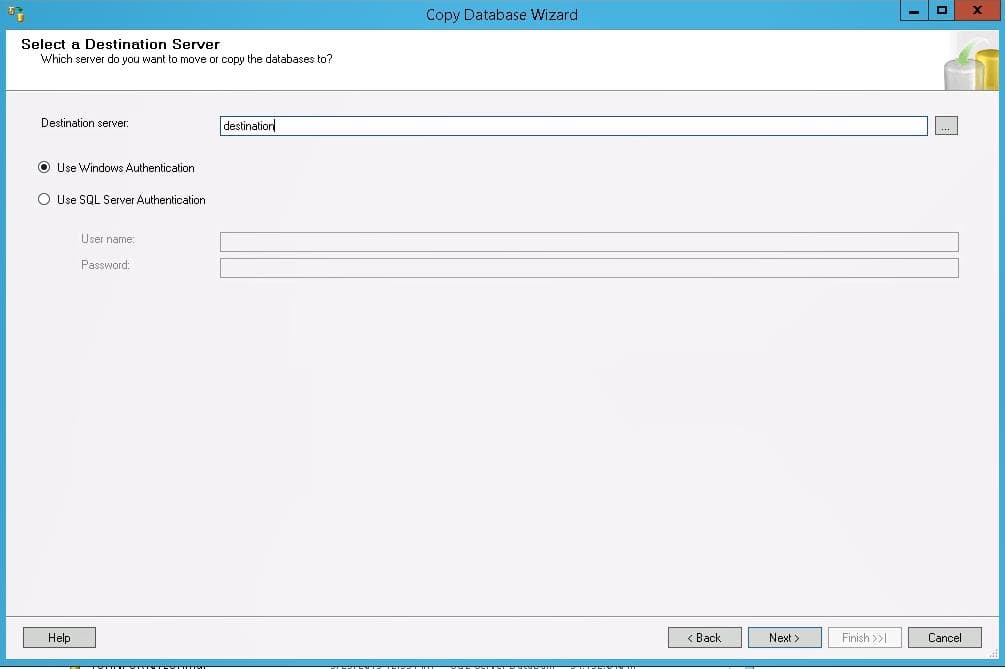
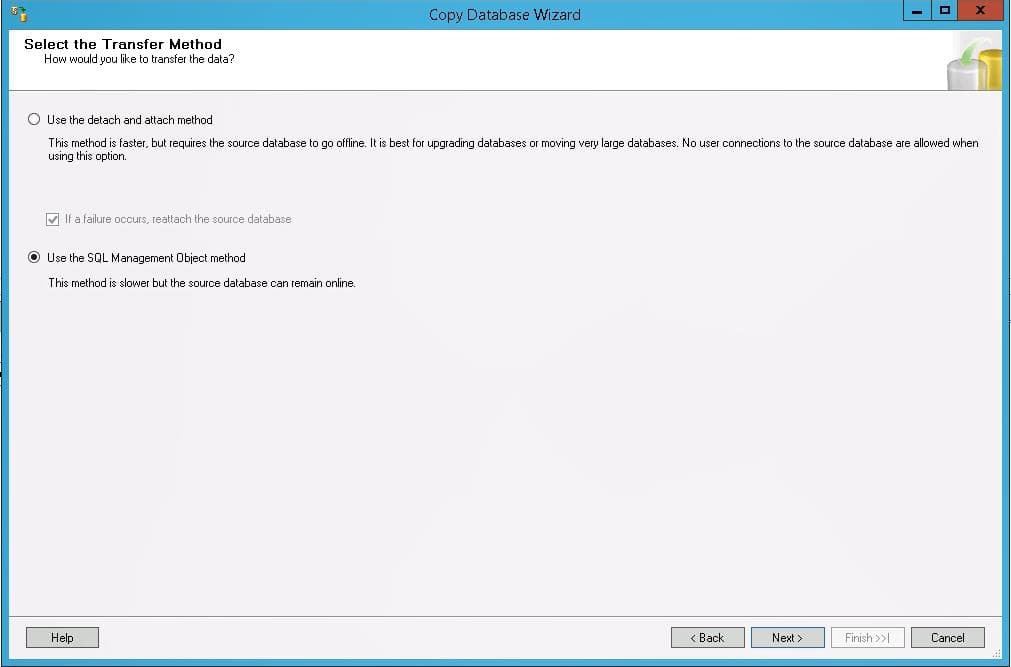
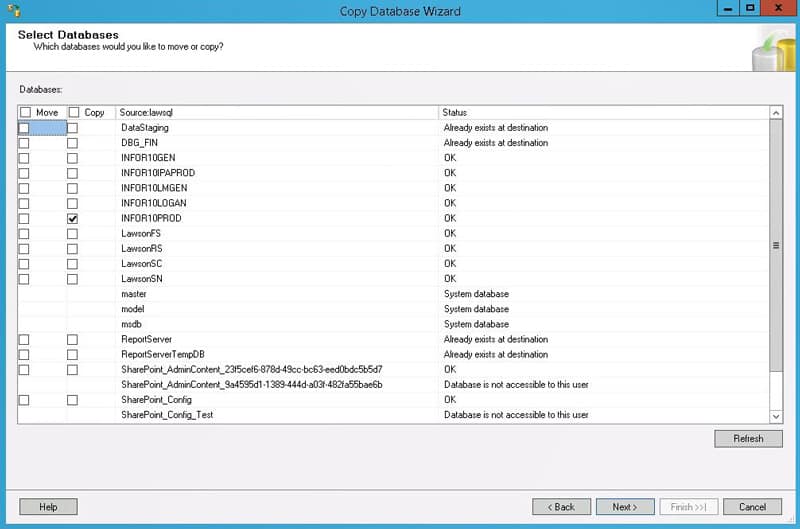
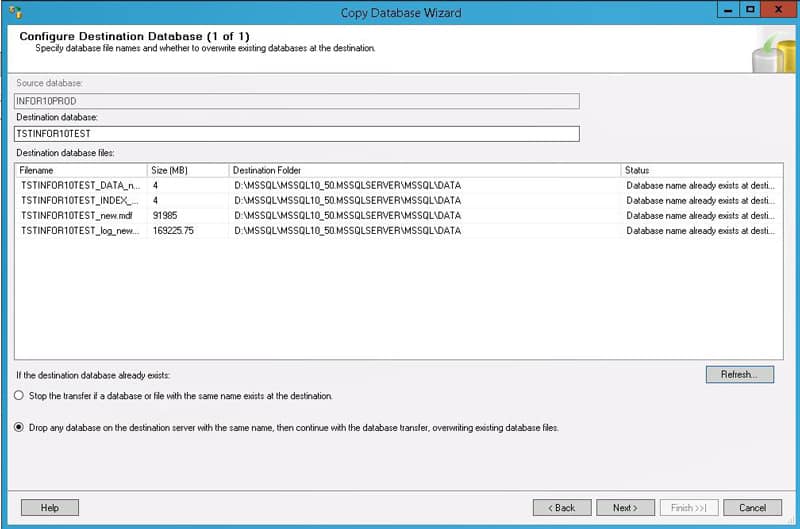
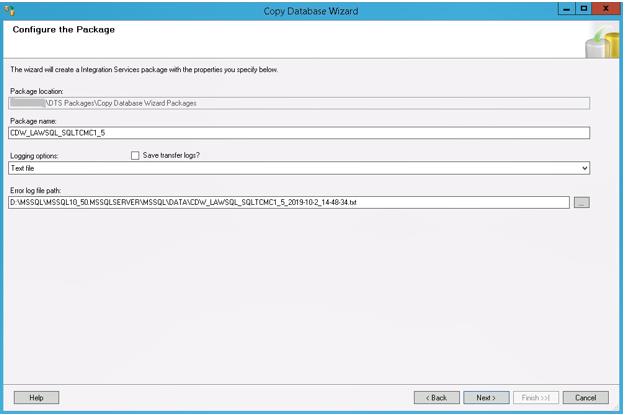
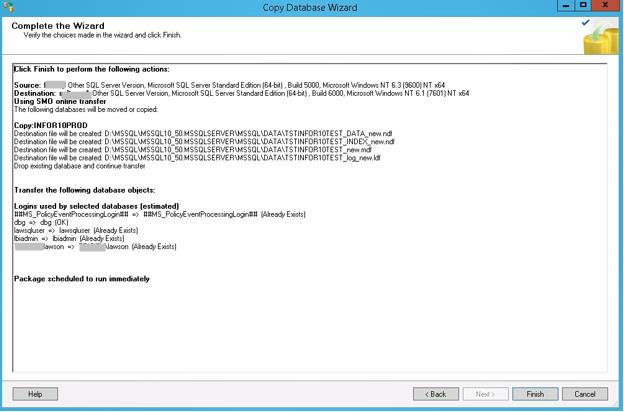
An alternative to a SQL database backup & restore is to use the Copy Database Wizard in SQL Server.
Right-click on the database, and select Copy. The source and destination can reside on different servers. You can opt to copy without taking the source database online. It will take longer, but it doesn’t require downtime. You can also copy to an existing database if you select the option to drop the database before adding if it exists. This tool is especially useful if you are trying to copy data from a new version of SQL Server to an older version such as 2008. We have come across that configuration many times in Lawson PROD to DEV environments.