LDAPS: Binding LDAP to IP Address or FQDN
While configuring LDAPS, if you try logging into Lawson, and it behaves as if your user doesn’t exist, check the LAWDIR/system/security_authen.log. You may encounter an error similar to this:
Could Not Bind With privileged identity.
Thu Dec 3 14:27:49.397 PST 2020 – default–1104671165 – L(2) : Failed to get DN for user: lawson
Thu Dec 3 14:27:49.428 PST 2020 – default–1104671165 – L(4) : Set Content-Security-Policy : script-src ‘self’ ‘unsafe-inline’ ‘unsafe-eval’
Thu Dec 3 14:27:56.977 PST 2020 – default–1104671165: Error encountered while getting users DN. Please see logs for details[peckb73unhe1fga2c54hqghqlj]Could Not Bind With privileged identity. User [lawson]simple bind failed: 111.111.111.11:3269
Stack Trace :
javax.naming.CommunicationException: simple bind failed: 111.111.111.11:3269 [Root exception is javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: No subject alternative names matching IP address 111.111.111.11 found]
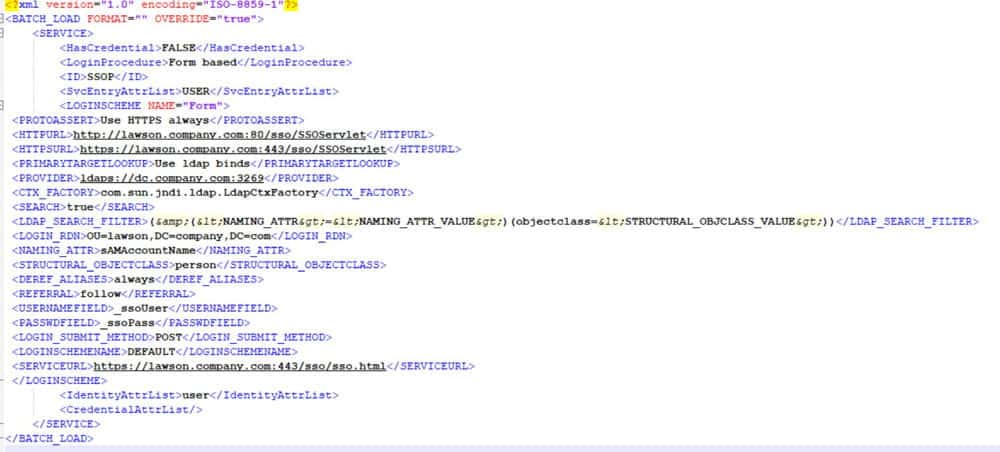
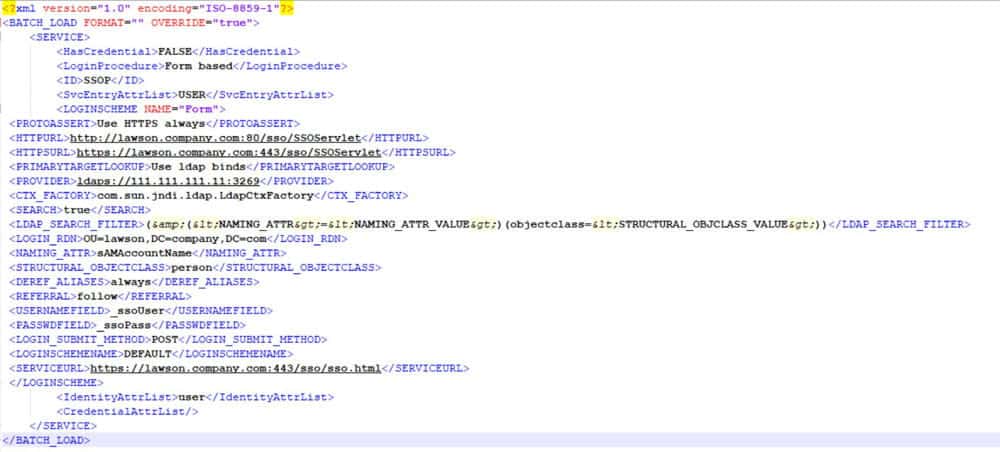
This means that the certificate on your Domain Controller to which Lawson is bound, has a Subject Alternative Name that does not match the DC IP address. You need to make sure the server name you are using for the bind matches the SAN on the Domain Controller’s certificate.
So, bind to this:
Instead of this: