Configuring Lawson and Landmark for LDAP Signing
Configuring Lawson and Landmark for LDAP Signing
Contents (Click on a Topic to Jump to Section)
- An Introduction to LDAPS
- Prerequisites
- LDAP Certificate – AD LDS
- 1 – Add the LDAP Certificate to the AD LDS Service
- 2 – Export Certificate (.cer) file
- 3 – Grant Permissions on Certificate Container
- 4 – Smoke Test
- LDAP Certificate – WebSphere
- LDAP Certificate – Java
- 1 – Add Certificate to OS Java (ikeyman example)
- 2 – Add Certificate to WebSphere Java (keytool example)
- Lawson Configuration Changes
- 1 – Update Authentication Data Store
- 2 – Update LDAP Bind Settings
- 3 – Smoke Test
- Landmark Configuration Changes
- 1 – Update LDAP Bind Settings
- 2 – Smoke Test
- Infor Federation Services (IFS) Configuration Changes
- Conclusion
An Introduction to LDAPS
LDAP Signing (LDAPS) provides a way of securing traffic between your applications and AD LDS or Active Directory. In the second half of 2020, Microsoft plans to release a patch that will enforce LDAPS traffic by default. You can get more information about the Microsoft KB here.
What does this mean for my applications?
Well, even if you are using AD FS for authentication, your applications will be impacted. Some pieces of Lawson, such as BPM, are still going to be bound to LDAP, as is the Rich Client login for Landmark. Also, Lawson still communicates with AD LDS, so that would be impacted as well. Note that if you are using IBM’s Tivoli Directory Server (IBMTDS) for your Authentication Data Store, you will not need to make any changes to the Authentication Data Store. However, you will need to make the LDAP Bind changes for any of your applications that use LDAP Bind.
What will happen if I don’t prepare?
If you don’t configure your Lawson and Landmark environments to accept LDAPS traffic, then you will experience some application failures in these areas:
- LASE will fail to start
- Logins that use LDAP bind will no longer be able to communicate
- Lawson Security Administrator
- BPM
- Microsoft Add-ins
- Landmark Rich Client
- IFS will no longer be able to sync users from Active Directory
When is this happening?
Microsoft has said they will release the patch that enforces LDAPS in the latter half of the year. They already released a patch in March that includes additional auditing and logging, and allows for enforcement via Group Policy. This update will not have a direct impact on your applications, and it is safe to take the update any time.
When should we make the configuration changes?
You can make the changes now, or any time before you take the LDAPS enforcement patch. There is not a negative impact on your applications if you make the changes now, and in fact, it is recommended that you do them as soon as you can.
Are any other applications affected?
No, the only applications affected are those that use LDAP Bind, or communicate with AD LDS. Applications like LBI or MSCM, which use DSP for authentication, will not be affected in any way.
What do we need to do?
Glad you asked! Here is a step-by-step guide for configuring your Lawson and Landmark environments for LDAPS. (NOTE: It is important that you follow these steps in order!! All of the certificate work MUST be done before the Lawson/Landmark configurations are done. Also, this document will indicate whether the work needs to be done in LSF only, Landmark only, or both.)
Prerequisites
Here is what you will need before you get started.
- SSL certificate for the AD LDS server with the private key (.pfx) included
- Note: Certificate must contain a SAN (Subject Alternate Name)
- Can be an existing wildcard cert, or the cert already installed on your LSF server (if it meets the requirements)
- You will also need to know your private key password for the cert
- ssoconfig password
- LDAP Bind password
- This is the password for the user in the LDAPBINDDN setting in your LAWDIR\system\install.cfg file
- Verify the port you are using for LDAPS (typically 636 or 3269)
- 636 is the standard SSL, 3269 is the Global Catalog Port
- Global Catalog is preferred when the LDAP servers support it
- Take snapshots of all your servers. Just do it!
LDAP Certificate – AD LDS
This procedure only has to be performed on the server that hosts AD LDS (most likely your LSF server).
1 – Add the LDAP Certificate to the AD LDS Service
- Identify the AD LDS service instance in your Microsoft Services list
- Launch MMC (Microsoft Management Console)
- Choose File > Add/Remove Snap-In
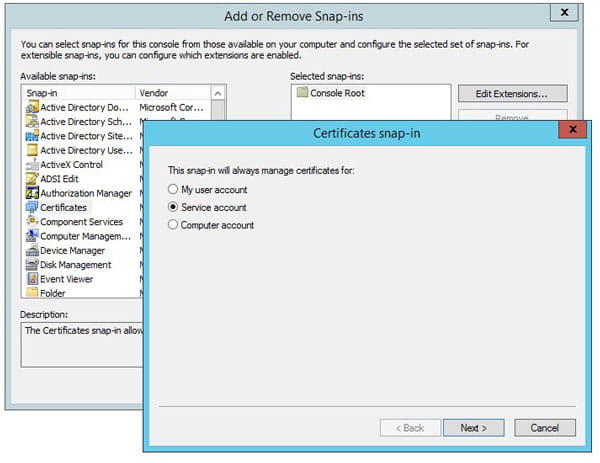
- Add the certificates Snap-In
- Choose “Service” account and click “Next”
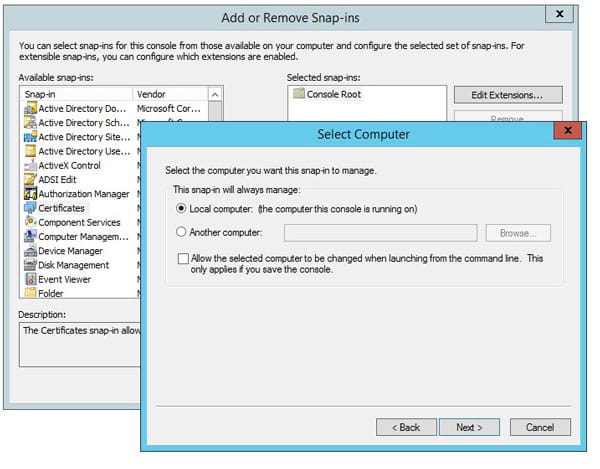
- Choose “Local Computer” and click “Next”
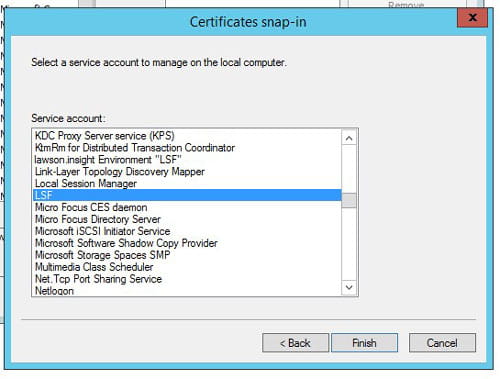
- Choose the Service Account you identified above and click “Finish”
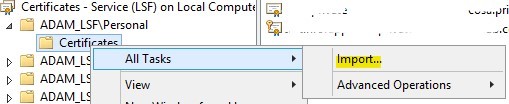
- Right-click on the service that was added and select “All Tasks > Import”
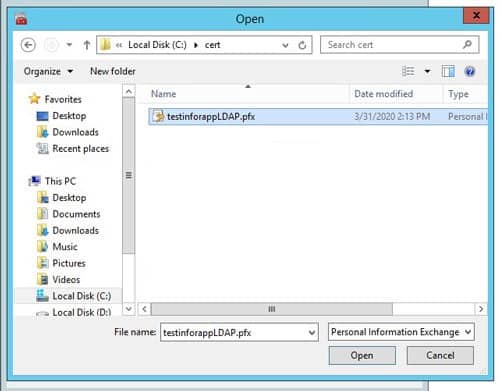
- Click next and browse to the .pfx certificate file. Click “Next”
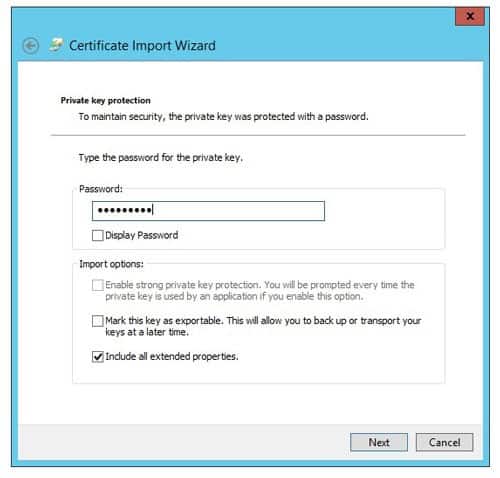
- Enter the private key password
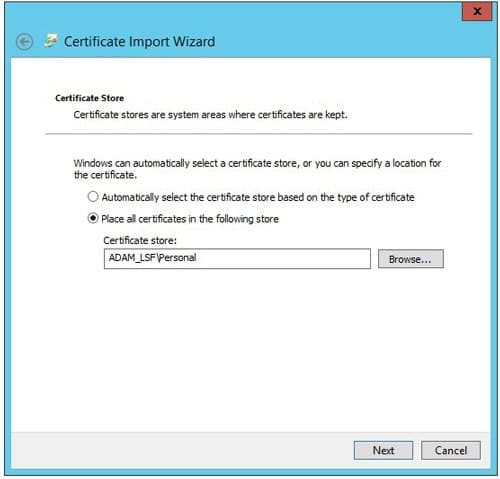
- Place the certificate in the Personal store for the AD LDS service
- Click Next then Finish
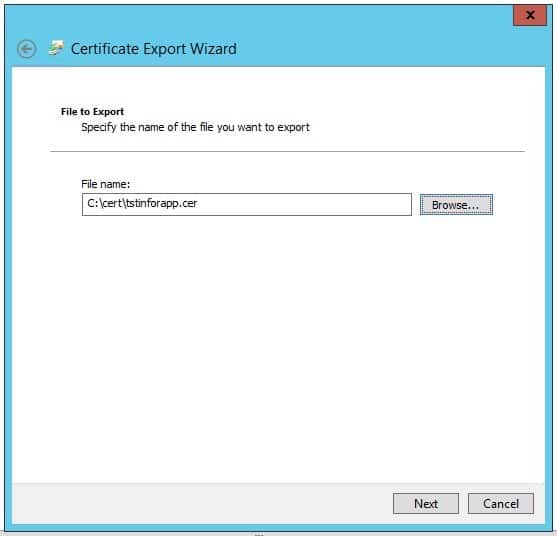
2 – Export Certificate (.cer) file
Export the certificate as a Base-64 encoded X.509 (.cer) for the OS and WebSphere Java updates.
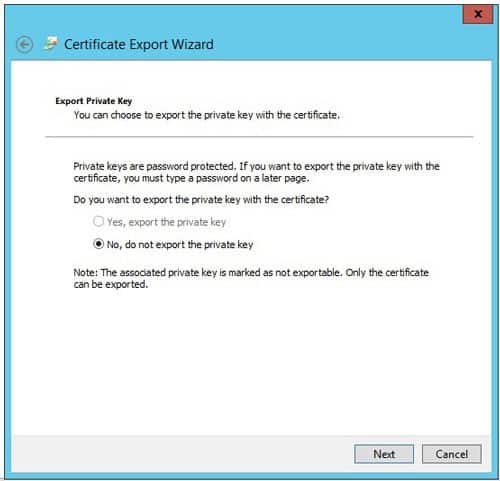
- In MMC, right click the certificate > All Tasks > Export and click Next
- Do not export the private key
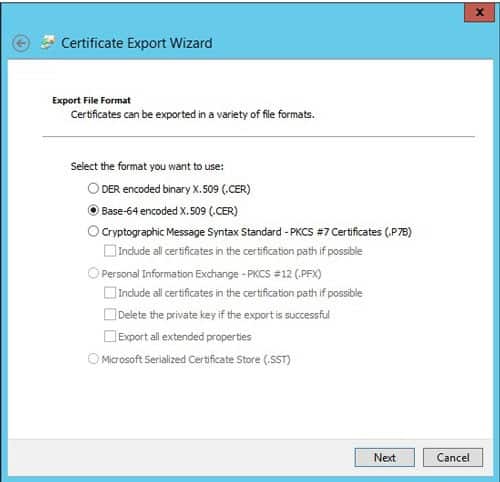
- Choose Base-64 encoded X.509 (.cer) and click Next
- Choose a location to save the file for later use
- Click finish
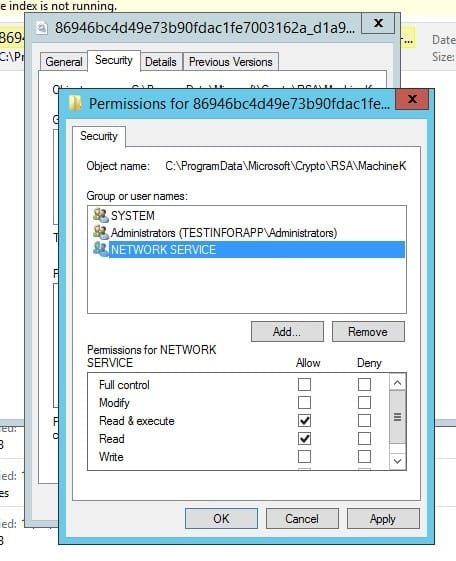
3 – Grant Permissions on Certificate Container
This is where you will need the service account that is running the AD LDS service (you made a note of that earlier). That user needs to be granted Read and Read & Execute permissions on the Unique Container file, as well as the Machine Keys directory.
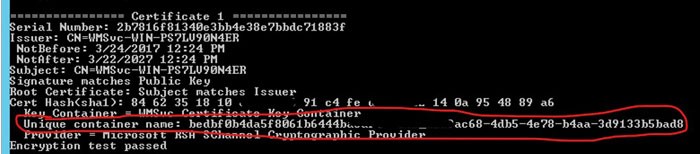
- From an administrator command window, run command certutil -store MY
- Find the LDAPS cert(s) by comparing the cert hash to the thumbprints on the certificate properties in MMC
- Make note of the Unique Container Name
- Navigate to the “Keys” or the “MachineKeys” folder
- This can be found in multiple places depending on your server configuration
- Some possible locations: C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys or C:\Documents and Settings\All Users\Application Data\Microsoft\Crypto\RSA\MachineKeys or C:\Documents and Settings\All Users\Application Data\Microsoft\Crypto\Keys
- You could also do a file search for the unique container name
- Grant Read and Read & Execute permissions on the Keys/MachineKeys directory AND the Unique Container file
- NOTE: if you have a nested certificate, you may have more than one unique container file. Grant permissions on all of the containers related to your LDAP Cert.
- Stop the LSF environment service
- Restart the AD LDS service
4 – Smoke Test
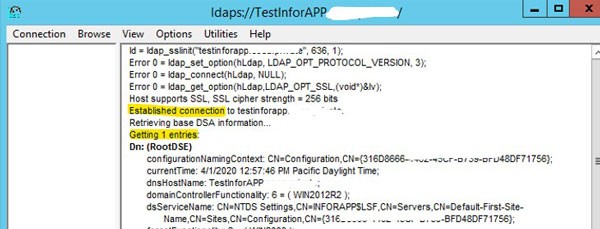
- Open the ldp.exe tool
- Type the server FQDN, SSL port, and check the SSL box
- Click “OK”
- Make sure a connection is established, and the tool finds an entry
- Do not proceed until you have a successful smoke test
LDAP Certificate – WebSphere
This procedure needs to be performed for both the Lawson and Landmark instances of WebSphere.
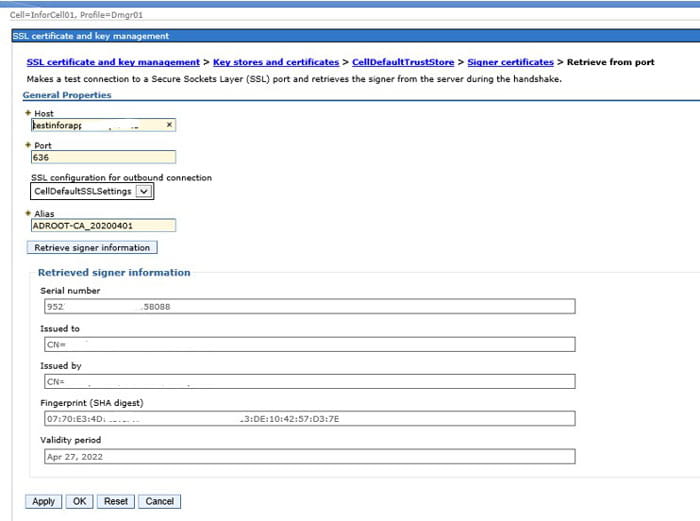
In this procedure, you are going to update the Default Trust Store on both the Cell and the Node in WebSphere. These instructions demonstrate how to get the LDAPS certificate into WebSphere using the “Retrieve from port” button. It’s the simplest way, but you do also have the option of manually adding the certificate file (.pfx) in each store.
- Access the WAS Admin Console and navigate to: Security > SSL certificate and key management > Key stores and certificates
- Click the CellDefaultTrustStore > Signer certificates
- Click the Retrieve from port button.
- Host: <the server where your LDAPs certificate was added to the AD LDS service>
- Port: <the port that your network team is using for LDAPS>
- Alias: <give it a meaningful name>
- Click Retrieve signer information.
- Once you click “Retrieve signer information”, the bottom of the form will be populated with information about your certificate.
- Click OK & save changes.
- Synchronize the nodes
- Perform these same steps for the NodeDefaultTrustStore
- Remember to do this in your WebSphere environment for both Landmark AND Lawson!
LDAP Certificate – Java
This procedure needs to be performed on both the Lawson AND Landmark servers.
Adding certificates to the Java store can be done using either the ikeyman GUI utility, or the keytool command line utility. The below instructions will demonstrate both methods. Whichever utility you use, the procedure is the same for both OS Java and WebSphere Java.
1 – Add Certificate to OS Java (ikeyman example)
This is the Java instance that is used by LSF or Landmark. Here is an example of updating cacerts using the ikeyman utility.
- Set environment variables (<APPINSTALLDIR>\enter)
- Run command “where java” to determine where LAW_JAVA_HOME is located
- NOTE: You may have multiple instances of Java, and you need to make sure you apply the cert to all of them!
- Back up file LAW_JAVA_HOME\jre\lib\security\cacerts
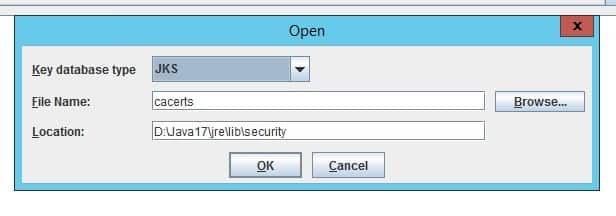
- Run the ikeyman utility at WAS_HOME/bin
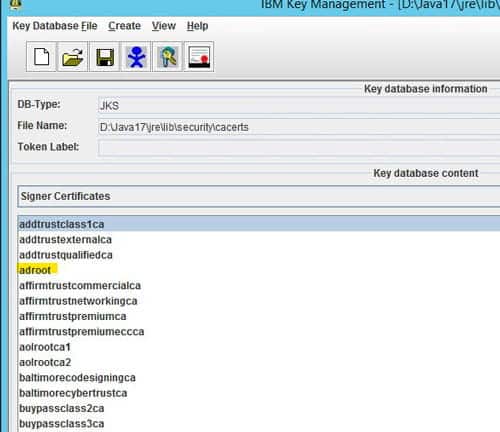
- Open the LAW_JAVA_HOME/jre/lib/cacerts file and select the Key database type of JKS
- Type password “changeit”
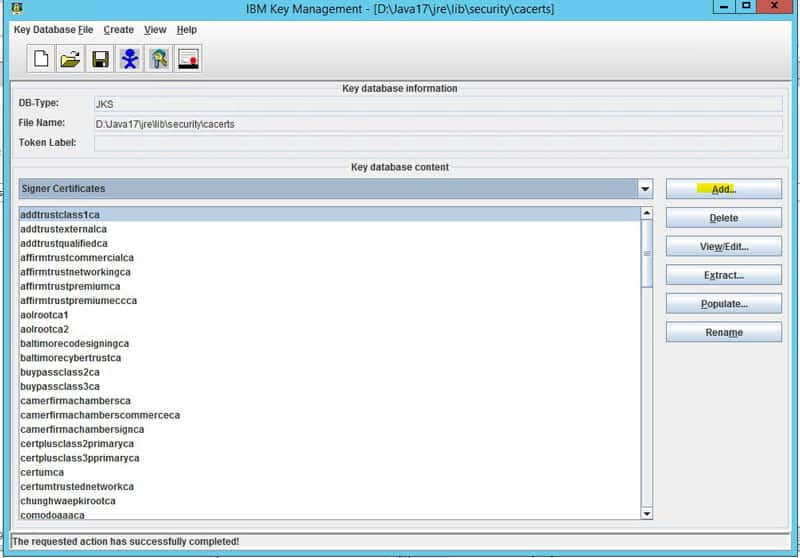
- Select “Signer Certificates” in the dropdown
- Click “add” and navigate to the ldap certificate exported earlier
- Give it a meaningful name
2 – Add Certificate to WebSphere Java (keytool example)
This is the Java instance that is installed with WebSphere. Here is an example of updating cacerts using the keytool utility. NOTE: You will most likely have more than one Java folder in the WebSphere install directory. It is important to update all instances.
- Find your WebSphere Java directories (may have multiple)
- Located at WAS_HOME
- “Base” java and version-specific java (i.e. WAS_HOME/Java and WAS_HOME/Java_1.7_64)
- Make note of these directories
- Back up the file(s) WAS_JAVA_HOME/jre/lib/security/cacerts
- Add signer certs using keytool command line utility
- Open an administrator command window
- Get a list of the existing certs and validate using command
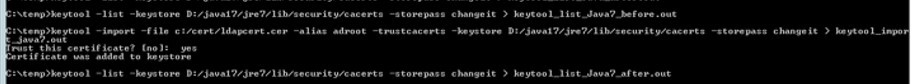
- keytool -list -keystore WAS_JAVA_HOME/lib/security/cacerts -storepass changeit > keytool_list_WS_before.out
- Import the new cert using the command
- keytool -import -file <file path to your .cer file> -alias <meaningful name> -trustcacerts -keystore WAS_JAVA_HOME/jre/lib/security/cacerts -storepass changeit > out
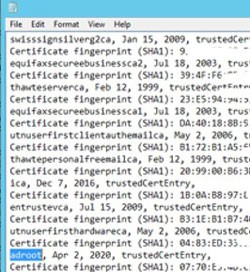
- Get the list of the existing certs and validate that the new cert was added using command
- Compare your “before” list to your “after” list to make sure the cert was added correctly
Don’t forget to do BOTH Lawson and Landmark!!
Lawson Configuration Changes
This procedure is performed only on the LSF Server
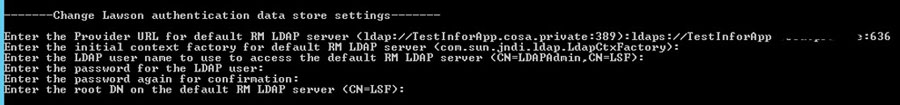
1 – Update Authentication Data Store
- Open an administrator command window or LID
- Set the environment variables
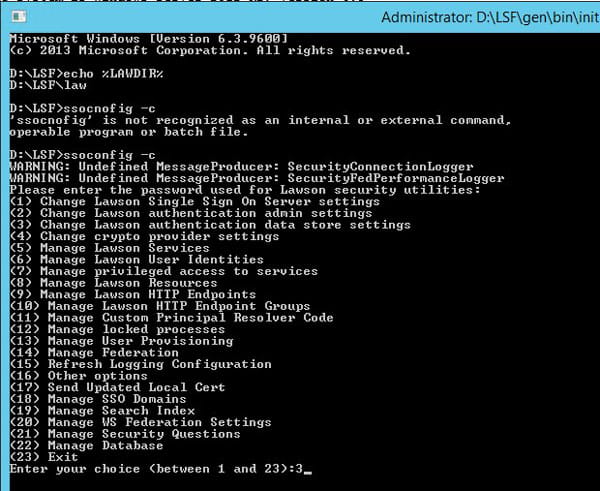
- Run the ssoconfig -c command
- Choose option “Change Lawson authentication data store settings”
- Update the protocol and port on the Provider URL
- Leave the next two values the same
- Enter the password for the LDAP user
- Confirm the password for the LDAP user
- Leave the last value the same
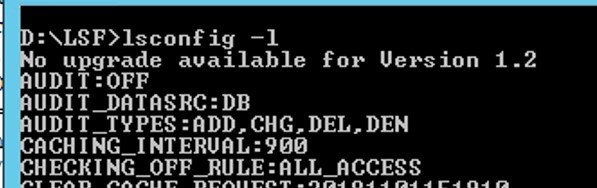
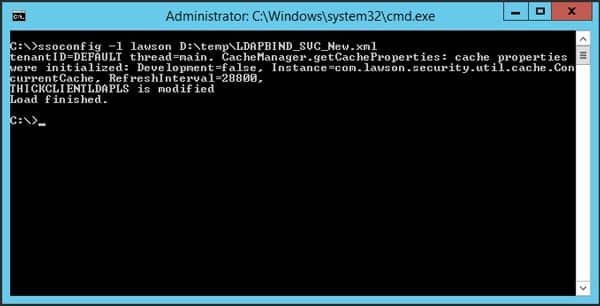
- Run lsconfig -l to smoke test
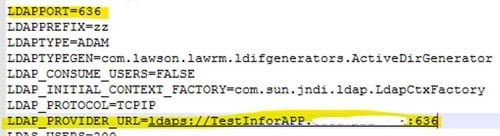
- Update the LAWDIR\system\install.cfg file with the new values so it will be ready for future patches
2 – Update LDAP Bind Settings
Export the LDAP Bind Service
- From an administrator command window or LID, run ssoconfig –c
- Select “Manage Lawson services” > “Export Service and identity info” > “NO”
- Enter the name of your LDAP Bind service (such as LDAP_BIND_SVC)
- Do not export the identities (NONE)
- Provide a filename
Update the LDAP Bind Service
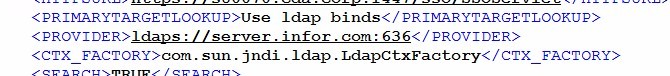
- Open the exported file
- Set the “Override” setting to “true”
- Locate the LDAP provider line and update the protocol and port
- Save the file
Upload the file to ssoconfig
- Run ssoconfig –l <SSOCONFIG_PASSORD> <FULL_FILE_PATH> from a command window or LID
- Restart the LSF server
3 – Smoke Test
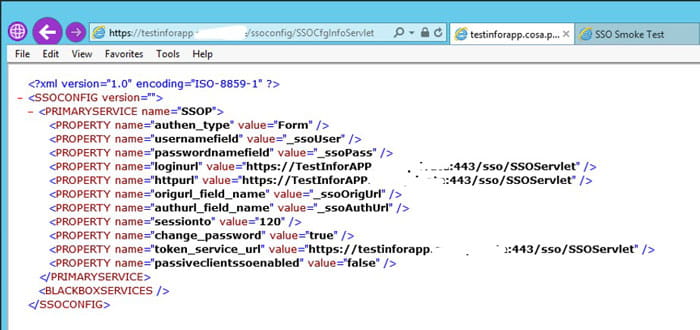
- Perform Lawson Authentication Smoke Tests
- https://server.company.com/ssoconfig/SSOCfgInfoServlet
- https://server.company.com/sso/SSOServlet
- Log into Lawson and perform a couple of inquiries/batch jobs
Landmark Configuration Changes
This procedure is performed only on the Landmark Server
1 – Update LDAP Bind Settings
- Launch Rich Client for the gen data area
- Search for Login in the search box
- Double click the Login Scheme business class
- Search for the LoginScheme that is associated with the LDAP Bind Service (you may have more than one)
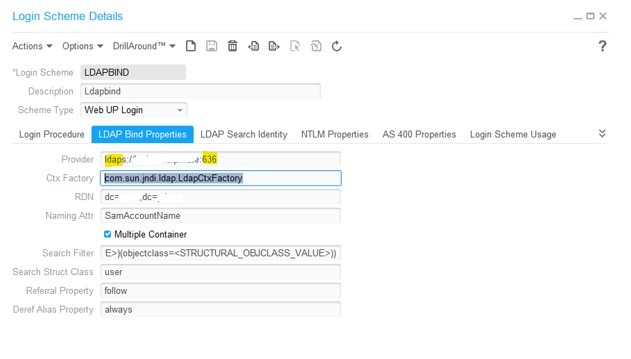
- Double click on the LoginScheme to open the properties screen
- Click the LDAP Bind Properties tab
- Click on the LDAP Bind Properties tab
- Update the port and protocol on the Provider entry
- Save the update
- Restart the Landmark Server
2 – Smoke Test
- Make sure you can still log into Rich Client using your AD username & password
- If you use IPA, it is also a good idea to run some IPA Smoke Tests to make sure that the authentication/communication between Landmark and Lawson is still functioning
- Web Run Node
- System Command Node
- File Access Node
- Lawson Query/Transaction Nodes
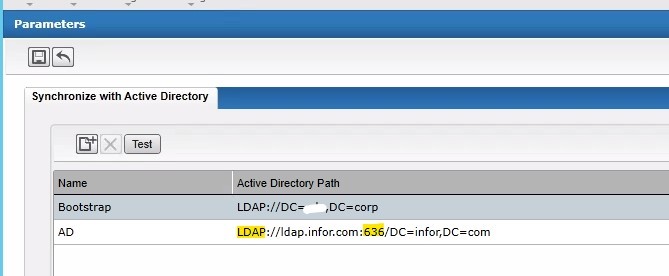
Infor Federation Services (IFS) Configuration Changes
This procedure is performed only on the IFS Web Utility, and is only required if you are using AD FS for authentication
- Ensure that a certificate for the AD server is present in your IFS Server’s Trusted Root Certificate Store
- Update the AD Configuration in IFS
- Make sure you can still synchronize users in IFS
Conclusion
And now you are ready to enforce LDAPS connections! Be sure to also watch the webinar that we gave on this topic April 16, 2020. You can find it in the education section on our website.
View Our Webinar “Configuring Lawson for LDAP Signing”